
When it comes to sending emails from your personal inbox or an email marketing tool, authentication is the first step you need to take. If you know how to copy-paste, you are already 50% there.
Authentication allows receiving inboxes and recipients to validate if the email sent from a particular domain is authentic and came from the right person or business. It is just like a bank asking you to confirm your identity before being able to help you with any requests. Without proof of identity, you might be able to deposit a check, but won’t be able to get the account balance. Maybe you have a long-term relationship with your bank, and the clerk recognizes you even without your driver’s license, allowing you to do a bit more. But without that proof of identity, you are very limited in what you can do and sometimes banks will outright turn you down without offering help. The same thing happens with your emails.
How to Authenticate?
In order to authenticate your sender email, you need to ensure you are sending from a domain-based email address. Authentication is performed on the domain level, meaning if you want to send a letter using a free email address such as @gmail.com or @yahoo.com, you won’t be able to authenticate them. This is because you don’t own the domains gmail.com or yahoo.com, on top of the fact that they’re shared with a lot of other users in the world.
Email authentication simply helps prove that you are the one who is sending a particular email. Inboxes care about keeping their customers safe and want to ensure they can recognize and differentiate legitimate senders from spoofers. Authentication is the first thing they will look at.
DKIM – The Safety Deposit Box Method
There are three forms of authentication that are very commonly used. The first one is DKIM. DKIM stands for “Domain Keys Identified Mail” and helps protect email senders and recipients from spam, spoofing, and phishing. When an email is signed with the DKIM key, it allows an inbox to confirm that you are the one who sent the email and you own the domain that was used to send it.
To understand how it works on a technical level, it is easiest to compare the DKIM method to a safety deposit box you can use at the bank. Many safety deposit boxes have a two-key system. One is owned by the bank and the other by you. Both keys have to work in order to ensure it opens and you can access the content. If one key doesn’t match, the safe won’t open.

You need a unique DKIM key from every tool you use that sends email using your domain. It’s as simple as copy/pasting the two values given by your tool to your DNS panel. If you have a website or have set up your personal inbox already – you have a DNS panel!
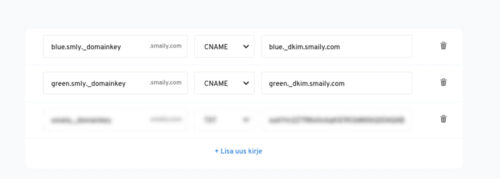
In practice, DKIM is a digital signature that is added to your email’s header when you press send and gets validated by the receiving inbox once your email arrives there. The digital signature includes two cryptographic hashes (header and message body) and information about how the digital signature was generated. This information is used by the receiving mail server to look up the sender’s public DKIM key (the one you pasted in your DNS panel) and to decrypt the signature in the email in order to compare the two. If they match, your email will be considered authenticated with DKIM.
SPF – The Power of Attorney Method
Authenticating your domain with all the tools that send emails using your domain is an important factor. Inboxes and recipients want to ensure that the emails are received from tools that have permission to do so. All the entries in your SPF record allow the receiving inbox to see if the email was sent from the appropriate IP addresses or not.
SPF validates and shows to an inbox that it was sent from an authorized mail server’s IPs. If you are sending emails from a specific email marketing service provider, they will provide DNS entries you need to add inside your DNS panel, which allows them to send emails on your behalf. Technically, that is what’s happening. When you buy a domain and send out emails from your personal business email using G Suite, for example, then the emails are being sent out by Gmail. If you use Smaily, then Smaily is the one that is sending your emails from their IPs.
SPF minimizes the risk of having others send emails pretending to come from your domain. SPF allows receiving inboxes to verify if the email came from IPs that have permission to send emails with your domain. Each root domain can have only one SPF record and only one for every subdomain.
yannatorry@smaily.com yt@smaily.com yannatorry@email.smaily.com yannatorry@transactional.smaily.com
If my organization had these 4 example emails above, the DNS panel would have 1 SPF record per root domain or sub-domain. One for smaily.com, email.smaily.com and transactional.smaily.com. If you have more than one SPF record per root domain or subdomain, your SPF and DMARC can fail.
Here is an example of a domain’s SPF record:
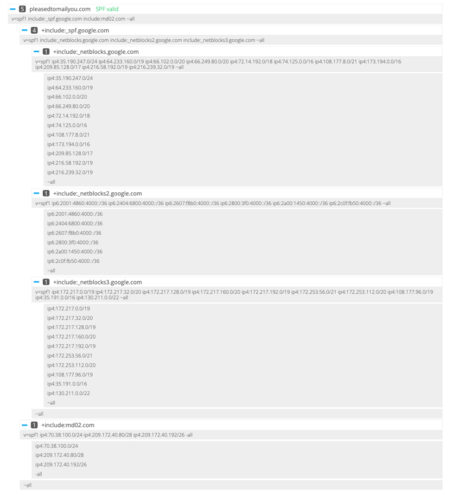
v=spf1 include:_spf.google.com include:md02.com ~all
The word “include” seen twice in the SPF record above, allow emails to be sent from Google and a specific email marketing tool. You can see in the screenshot below that for every “include” a series of IP addresses are associated. These are the IP addresses that emails are allowed to be sent out from.
SPF can be compared to giving Power of attorney to your spouse, parents, or your accountant. Anyone can try to go to the bank pretending to be you, but the ones that have power of attorney can be validated with the bank and will have access to do things on your behalf.
DMARC – The Fraud Detection System
The third form of authentication that is extremely helpful and interesting is DMARC. DMARC stands for “Domain-Based Message Authentication Reporting And Performance”. And as you can imagine, this helps protect email senders and their recipients from spoofed emails.
What is so interesting about DMARC is that it allows you to tell the inboxes what to do with emails that don’t have a passing SPF or DKIM key. You can let your subscriber’s receiving inbox decide what to do with an email if you set a policy of “none“. You can also let the receiving inbox know that you would prefer unauthenticated emails to go to the spam folder or to block them completely with a policy of “quarantine “or “reject“. It’s like your very own personal fraud department that alerts you when you are being spoofed.
You don’t want others to be sending out emails using your domain, as this will affect your domain reputation and your deliverability. Your sender reputation can get affected, as you don’t know what they are sending out. You might not be aware of the tools that are being used to send emails out. When it comes to authentication, senders think of the most obvious tools that send emails, such as personal inboxes or an email marketing tool. Don’t forget that there are a lot more tools that can be sending emails using your domain, such as accounting systems or calendar invites! These emails’ inbox placement will be affected if you do not ensure they are authenticated, especially if you have a strong DMARC policy in place!
DMARC’s Benefits for You
A bank is constantly monitoring what is happening with your accounts or credit cards and will notify you the moment things aren’t right. If there is an activity that they can not explain or understand, they will block the payment and ask you what you want to do. Do you want to let the payment pass or not? Similar principles apply when using DMARC to authenticate your domain.
With DMARC in place, you will be getting daily emails that are generated from receiving inboxes such as Google or Hotmail. They will include information such as the reason they failed DMARC (might be a broken DKIM key) and from which IP they were sent. Just like with a credit card and fraud, you want to ensure you know when your identity is being used as it. DMARC reports allows you to investigate and fix issues. When starting it is important to set the policy to “none”. This ensures you give yourself the time to catch all the emails that you are actually sending that are not authenticated and fix the issue.
How to move on from here?
Understanding why email authentication is important is the first step. The second one is making a list of all the tools that you know of that send emails or notifications using your sender domain. A quick search in the knowledge base or settings of these tools will help you gather all the DNS entries you will need to copy-paste in your DNS panel. You can find the Smaily entries here.
If you are unsure of what to copy-paste where feel free to communicate with your hosting provider or email marketing tool. With a list of all the DKIM, SPF, and DMARC keys you need to add, they will be able to help you do this quickly or ensure it is implemented correctly. It is a very quick procedure.
If you can’t find the help you are looking for, feel free to contact your support team at Smaily or sign up here to get it done for free without solicitation at Let’s Authenticate the World.
About the Author
Yanna-Torry Aspraki is a CBDO & Deliverability Specialist at EmailConsul.
Sitting on the executive team at the intersection of Product, Growth, and Sales, YT helps drive the company forward in a market in desperate need of accessible and reliable deliverability tools, while representing EmailConsul in places email & deliverability have never been before.
